十、dashboard部署及访问控制
10.1 dashboard部署
项目地址:https://github.com/kubernetes/dashboard
本文中部署的是v2.0.0版本
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
|
[root@k8s-master dashbad]$ kubectl apply -f https://raw.githubusercontent.com/kubernetes/dashboard/v2.0.0/aio/deploy/recommended.yaml
[root@k8s-master dashbad]$ kubectl get pods -n kubernetes-dashboard
NAME READY STATUS RESTARTS AGE
dashboard-metrics-scraper-c79c65bb7-s9qf5 1/1 Running 0 3h6m
kubernetes-dashboard-56484d4c5-tf6rj 1/1 Running 0 3h6m
[root@k8s-master dashbad]$ kubectl get svc -n kubernetes-dashboard
NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
dashboard-metrics-scraper ClusterIP 10.108.156.169 <none> 8000/TCP 3h6m
kubernetes-dashboard ClusterIP 10.111.160.112 <none> 443/TCP 3h6m
[root@k8s-master dashbad]$ kubectl edit svc -n kubernetes-dashboard kubernetes-dashboard
spec:
......
type: NodePort
......
[root@k8s-master dashbad]
NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
dashboard-metrics-scraper NodePort 10.108.156.169 <none> 8000:31446/TCP 3h11m
kubernetes-dashboard NodePort 10.111.160.112 <none> 443:31962/TCP 3h11m
|
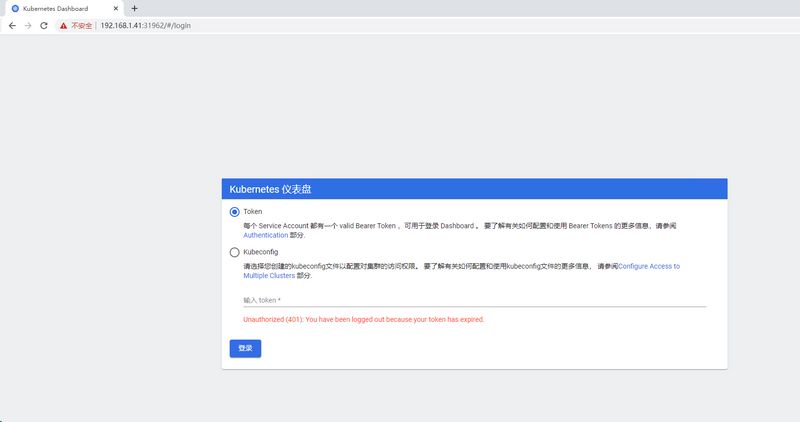
浏览器访问:https://192.168.1.41:31962/,如图:**这里需要注意的是谷歌浏览器会禁止不安全证书访问,建议使用火狐浏览器,并且需要在高级选项中添加信任**
10.2 基于Token的认证方式
最终实现:生成的token登陆dashboard后只能管理default名称空间的所有资源,其他任意名称空间均无任何权限
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
|
[root@k8s-master /]$ kubectl create serviceaccount default-ns-admin-sa -n default
serviceaccount/default-ns-admin-sa created
[root@k8s-master /]$ kubectl create rolebinding deafult-ns-admin-rolebinding --clusterrole=cluster-admin --serviceaccount=default:default-ns-admin-sa
rolebinding.rbac.authorization.k8s.io/deafult-ns-admin-rolebinding created
[root@k8s-master /]$ kubectl describe serviceaccount default-ns-admin-sa
Name: default-ns-admin-sa
Namespace: default
Labels: <none>
Annotations: <none>
Image pull secrets: <none>
Mountable secrets: default-ns-admin-sa-token-2k2h2
Tokens: default-ns-admin-sa-token-2k2h2
Events: <none>
[root@k8s-master /]$ kubectl describe secrets default-ns-admin-sa-token-2k2h2
Name: default-ns-admin-sa-token-2k2h2
Namespace: default
Labels: <none>
Annotations: kubernetes.io/service-account.name: default-ns-admin-sa
kubernetes.io/service-account.uid: 3f6ff5ad-ab33-43cb-a128-855b4e4c6e6b
Type: kubernetes.io/service-account-token
Data
====
ca.crt: 1025 bytes
namespace: 7 bytes
token: eyJhbGciOiJSUzI1NiIsImtpZCI6ImZvUkdraEJzT0x4dFNTSWhwV1A5Tml1QlhnOVVVMHR0ZTg3Vk8tVlN6VDAifQ.eyJpc3MiOiJrdWJlcm5ldGVzL3NlcnZpY2VhY2NvdW50Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9uYW1lc3BhY2UiOiJkZWZhdWx0Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9zZWNyZXQubmFtZSI6ImRlZmF1bHQtbnMtYWRtaW4tc2EtdG9rZW4tMmsyaDIiLCJrdWJlcm5ldGVzLmlvL3NlcnZpY2VhY2NvdW50L3NlcnZpY2UtYWNjb3VudC5uYW1lIjoiZGVmYXVsdC1ucy1hZG1pbi1zYSIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VydmljZS1hY2NvdW50LnVpZCI6IjNmNmZmNWFkLWFiMzMtNDNjYi1hMTI4LTg1NWI0ZTRjNmU2YiIsInN1YiI6InN5c3RlbTpzZXJ2aWNlYWNjb3VudDpkZWZhdWx0OmRlZmF1bHQtbnMtYWRtaW4tc2EifQ.TRqEtOXgEPgFzgsrBQge1VfvMuq0LitNB2n-nAd9oDd_VVIsCsKPI2IIIKbomvBWo7nYRG2UX4WQ_cz-qAQnprQY39JXpm5XSBX9Hoe1aII596djBmt8d5vhWfset1krWQWB-r8PeoTm3IpRzgOtZd4xUHSMCaY0LovlQssIYDEkIaHPr2vBoDq2UgCbNd0Rk1hf-XLyG3QGHeJBSGBe8ARhZfY9Kz5w5W8Dl5Bqravw6rvstHBWw_g5j6gbwlaRKjeY_fqhXUT5Q08dZGwD1105I0aw2qgoO8rEECfwVMA0sCbL0SmfxW22MLG5iY9lSdQloa7iacdYfthLhNwxcQ
|
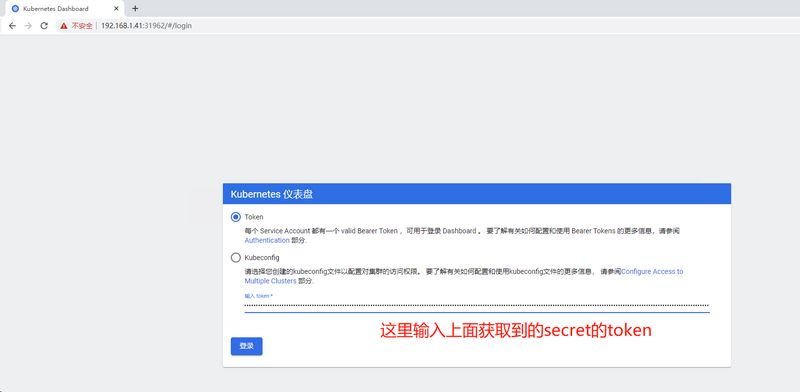
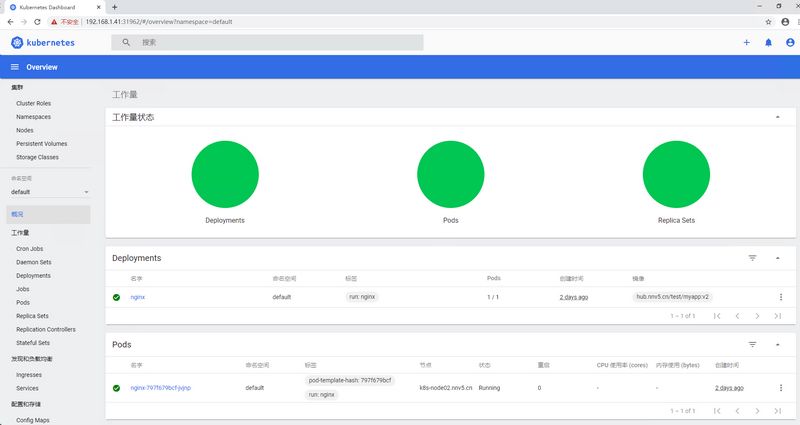
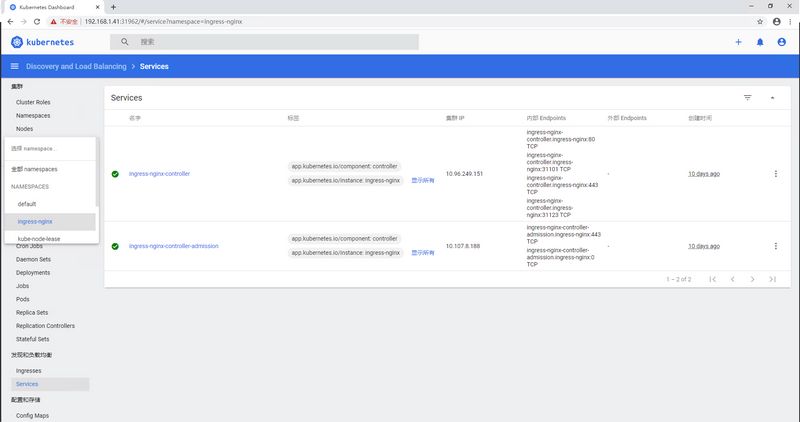
将该token复制后,填入验证,要知道的是,该token认证仅可以查看default名称空间的内容,如下图:
10.3 基于kubeconfig认证方式
最终实现效果:生成的配置文件登陆dashboard后,可以管理整个集群。
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
|
[root@k8s-master /]$ kubectl create serviceaccount default-ns--kubeconfig-admin -n default
serviceaccount/default-ns--kubeconfig-admin created
[root@k8s-master /]$ kubectl create clusterrolebinding default-ns--kubeconfig-admin-clusterrolebiding --clusterrole=cluster-admin --serviceaccount=default:default-ns--kubeconfig-admin
clusterrolebinding.rbac.authorization.k8s.io/default-ns--kubeconfig-admin-clusterrolebiding created
[root@k8s-master /]$ kubectl get secrets default-ns--kubeconfig-admin-token-mhwct -o jsonpath={.data.token} |base64 -d
eyJhbGciOiJSUzI1NiIsImtpZCI6ImZvUkdraEJzT0x4dFNTSWhwV1A5Tml1QlhnOVVVMHR0ZTg3Vk8tVlN6VDAifQ.eyJpc3MiOiJrdWJlcm5ldGVzL3NlcnZpY2VhY2NvdW50Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9uYW1lc3BhY2UiOiJkZWZhdWx0Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9zZWNyZXQubmFtZSI6ImRlZmF1bHQtbnMtLWt1YmVjb25maWctYWRtaW4tdG9rZW4tbWh3Y3QiLCJrdWJlcm5ldGVzLmlvL3NlcnZpY2VhY2NvdW50L3NlcnZpY2UtYWNjb3VudC5uYW1lIjoiZGVmYXVsdC1ucy0ta3ViZWNvbmZpZy1hZG1pbiIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VydmljZS1hY2NvdW50LnVpZCI6ImM0YTY0YjI1LWFjZjQtNDg0Yi1hYWZjLTA3M2U3MTUyZWUzNyIsInN1YiI6InN5c3RlbTpzZXJ2aWNlYWNjb3VudDpkZWZhdWx0OmRlZmF1bHQtbnMtLWt1YmVjb25maWctYWRtaW4ifQ.f0gsb0XFv9kjA_kZsBdzkZBH2RmA5VdNRW9_cHSYcK0osDF1RkPEfi7M-H7AcpRVqHVPwQGIHGTumFlg_eTN4z290tsAD8WxjFFBEyCL1SFxz4Hyl4j6Z-z3kbKbnW0Q9TyzKGnhxB8Vo3rfRcY58klmxkwPVUAmpCbYCZg3wVu6F3RxY5RaRJ2aPPZenOcgA_u0J-zHq8LpXC7dL5bcbWa9aDSMwAvzl5zQCXhciV_SKqhr80BIyAW9lYIsJsvJSdmJHmCD8Cp2ajldkKn2hDaDxQOhIv9NIlI1ebVY-omfJx8Mr9PLE3Si2F-lpBEMoBgV3-Hf9cnLrQexM0b_6w
[root@k8s-master /]$ kubectl config set-credentials default-ns--kubeconfig-admin --token=eyJhbGciOiJSUzI1NiIsImtpZCI6ImZvUkdraEJzT0x4dFNTSWhwV1A5Tml1QlhnOVVVMHR0ZTg3Vk8tVlN6VDAifQ.eyJpc3MiOiJrdWJlcm5ldGVzL3NlcnZpY2VhY2NvdW50Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9uYW1lc3BhY2UiOiJkZWZhdWx0Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9zZWNyZXQubmFtZSI6ImRlZmF1bHQtbnMtLWt1YmVjb25maWctYWRtaW4tdG9rZW4tbWh3Y3QiLCJrdWJlcm5ldGVzLmlvL3NlcnZpY2VhY2NvdW50L3NlcnZpY2UtYWNjb3VudC5uYW1lIjoiZGVmYXVsdC1ucy0ta3ViZWNvbmZpZy1hZG1pbiIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VydmljZS1hY2NvdW50LnVpZCI6ImM0YTY0YjI1LWFjZjQtNDg0Yi1hYWZjLTA3M2U3MTUyZWUzNyIsInN1YiI6InN5c3RlbTpzZXJ2aWNlYWNjb3VudDpkZWZhdWx0OmRlZmF1bHQtbnMtLWt1YmVjb25maWctYWRtaW4ifQ.f0gsb0XFv9kjA_kZsBdzkZBH2RmA5VdNRW9_cHSYcK0osDF1RkPEfi7M-H7AcpRVqHVPwQGIHGTumFlg_eTN4z290tsAD8WxjFFBEyCL1SFxz4Hyl4j6Z-z3kbKbnW0Q9TyzKGnhxB8Vo3rfRcY58klmxkwPVUAmpCbYCZg3wVu6F3RxY5RaRJ2aPPZenOcgA_u0J-zHq8LpXC7dL5bcbWa9aDSMwAvzl5zQCXhciV_SKqhr80BIyAW9lYIsJsvJSdmJHmCD8Cp2ajldkKn2hDaDxQOhIv9NIlI1ebVY-omfJx8Mr9PLE3Si2F-lpBEMoBgV3-Hf9cnLrQexM0b_6w --kubeconfig=/root/default-ns--kubeconfig-admin.conf
User "default-ns--kubeconfig-admin" set.
[root@k8s-master /]$ kubectl config set-context default-ns--kubeconfig-admin@kubernetes --cluster=kubernetes --user=default-ns--kubeconfig-admin --kubeconfig=/root/default-ns--kubeconfig-admin.conf
Context "default-ns--kubeconfig-admin@kubernetes" created.
[root@k8s-master /]$ kubectl config view --kubeconfig=/root/default-ns--kubeconfig-admin.conf
apiVersion: v1
clusters: []
contexts:
- context:
cluster: kubernetes
user: default-ns--kubeconfig-admin
name: default-ns--kubeconfig-admin@kubernetes
current-context: default-ns--kubeconfig-admin@kubernetes
kind: Config
preferences: {}
users:
- name: default-ns--kubeconfig-admin
user:
token: eyJhbGciOiJSUzI1NiIsImtpZCI6ImZvUkdraEJzT0x4dFNTSWhwV1A5Tml1QlhnOVVVMHR0ZTg3Vk8tVlN6VDAifQ.eyJpc3MiOiJrdWJlcm5ldGVzL3NlcnZpY2VhY2NvdW50Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9uYW1lc3BhY2UiOiJkZWZhdWx0Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9zZWNyZXQubmFtZSI6ImRlZmF1bHQtbnMtLWt1YmVjb25maWctYWRtaW4tdG9rZW4tbWh3Y3QiLCJrdWJlcm5ldGVzLmlvL3NlcnZpY2VhY2NvdW50L3NlcnZpY2UtYWNjb3VudC5uYW1lIjoiZGVmYXVsdC1ucy0ta3ViZWNvbmZpZy1hZG1pbiIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VydmljZS1hY2NvdW50LnVpZCI6ImM0YTY0YjI1LWFjZjQtNDg0Yi1hYWZjLTA3M2U3MTUyZWUzNyIsInN1YiI6InN5c3RlbTpzZXJ2aWNlYWNjb3VudDpkZWZhdWx0OmRlZmF1bHQtbnMtLWt1YmVjb25maWctYWRtaW4ifQ.f0gsb0XFv9kjA_kZsBdzkZBH2RmA5VdNRW9_cHSYcK0osDF1RkPEfi7M-H7AcpRVqHVPwQGIHGTumFlg_eTN4z290tsAD8WxjFFBEyCL1SFxz4Hyl4j6Z-z3kbKbnW0Q9TyzKGnhxB8Vo3rfRcY58klmxkwPVUAmpCbYCZg3wVu6F3RxY5RaRJ2aPPZenOcgA_u0J-zHq8LpXC7dL5bcbWa9aDSMwAvzl5zQCXhciV_SKqhr80BIyAW9lYIsJsvJSdmJHmCD8Cp2ajldkKn2hDaDxQOhIv9NIlI1ebVY-omfJx8Mr9PLE3Si2F-lpBEMoBgV3-Hf9cnLrQexM0b_6w
|
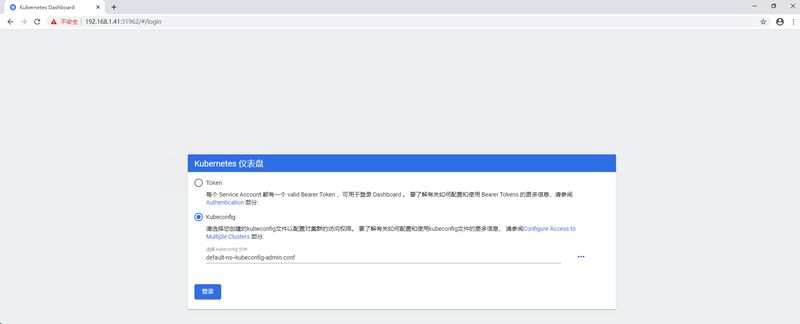
因为此配置文件所使用的serviceaccount中token是使用clusterrolebinding绑定到了clusterrole上面,所以拥有整个集群的管理员权限
10.4 基于basic账号密码认证
默认安装完k8s集群和Dashboard之后都是使用token登录的,这样使用起来不是很方便,每次登录还要找到token才能登录。
本片文章使用用户和密码方式进行登录!
环境介绍
| 集群环境 |
集群版本 |
搭建方式 |
dashboard的版本 |
| master |
v1.16.9 |
kubeadm |
kubernetesui_dashboard:v2.0.0 |
| node1 |
v1.16.9 |
kubeadm |
kubernetesui_dashboard:v2.0.0 |
| node2 |
v1.16.9 |
kubeadm |
kubernetesui_dashboard:v2.0.0 |
注意事项:
如果你的环境内不止一个master,那basic-auth-file这个文件要在每一个master上生成,并保证路径及内容和其他master一致!并且每个master都要修改kube-apiserver.yaml文件!
创建用户认证文件
1
2
3
4
5
|
[root@k8s-master ~]$ cat >> /etc/kubernetes/pki/basic_auth_file <<EOF
admin,admin,1
EOF
|
修改apiserver配置添加密码验证文件路径
1
2
3
4
5
6
7
8
9
10
11
12
|
[root@k8s-master ~]$ vim /etc/kubernetes/manifests/kube-apiserver.yaml
spec:
containers:
- command:
- --basic-auth-file=/etc/kubernetes/pki/basic_auth_file
[root@k8s-master ~]$ cd /etc/kubernetes/manifests/
[root@k8s-master manifests]$ mv ./kube-apiserver.yaml ../
[root@k8s-master manifests]$ mv ../kube-apiserver.yaml ./
[root@k8s-master manifests]$ kubectl apply -f kube-apiserver.yaml
|
创建clusterrolebinding为用户授权
1
2
3
|
[root@k8s-master manifests]$ kubectl create clusterrolebinding basic-dashboard-cluster-admin --clusterrole=cluster-admin --user=admin
clusterrolebinding.rbac.authorization.k8s.io/basic-dashboard-cluster-admin created
|
修改dashboard配置开启basic验证
1
2
3
4
5
6
7
8
9
10
|
[root@k8s-master dashbad]$ vim recommended.yaml
args:
- --auto-generate-certificates
- --namespace=kubernetes-dashboard
- --authentication-mode=basic
[root@k8s-master dashbad]$ kubectl apply -f recommended.yaml
|
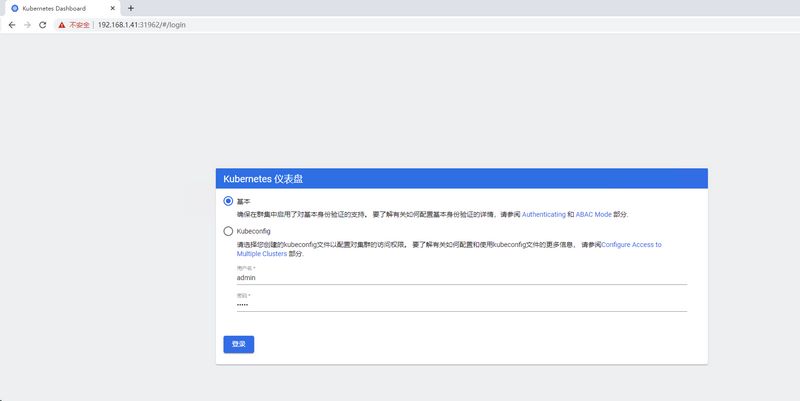
访问验证
浏览器访问https://192.168.1.41:31962/ 基本验证中输入 basic_auth_file 文件中设置的账号密码即可。
登陆后所拥有的权限为clusterbinding中绑定的clusterrole中定义的权限。

总结
以上均为kubeadm方式部署的集群。如果是二进制方式部署的集群,则不用在kubernetes-dashboard.yaml文件中开启authentication-mode=basic
basic验证方式存在一个问题,就是用户名和密码要保持一致,如果用户名和密码不一致,登陆验证的时候会提示Unauthorized (401): Invalid credentials provided(不要问我为什么,这个问题我也不知道咋解决)
另外/etc/kubernetes/pki/basic_auth_file文件不会热更新,每次添加新用户之后都需要手动重启一下api-server一般来说,只有一个用户就够了。












